In today’s digital-first world, cyber threats are evolving faster than ever before. Attackers are no longer relying only on brute force — they use sophisticated methods to blend into normal traffic, making detection extremely challenging. This is where BinaryFlux steps in. As a cutting-edge cybersecurity company, BinaryFlux has been doing tremendous work in protecting enterprises […]
In today’s digital-first world, cyber threats are evolving faster than ever before. Attackers are no longer relying only on brute force — they use sophisticated methods to blend into normal traffic, making detection extremely challenging.
This is where BinaryFlux steps in.
As a cutting-edge cybersecurity company, BinaryFlux has been doing tremendous work in protecting enterprises against advanced threats. With its powerful detection and analytics capabilities, it not only identifies attacks but also makes them easy to understand for customers through clear, intuitive visualizations.
Powerful Features That Tackle Modern Threats
BinaryFlux uses behavior learning and anomaly detection to continuously analyze patterns within network and user activity. Some of its most impactful detection use cases include:
Rarity Detection
Spotting unusual events that deviate from a user’s or system’s normal behavior — such as logins from unknown devices or first-time connections to rare endpoints.
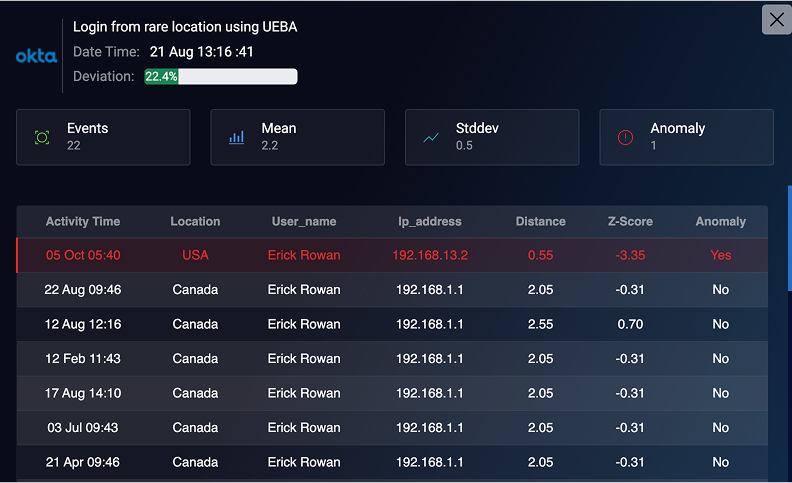
Examples:
- An employee suddenly accessing a database they’ve never used before.
- A server connecting to an IP address that no other system in the organization has communicated with.
- A user downloading files at 3 AM when they normally work only during office hours.
- A new process executing on a machine that has never run before.
Spike Detection
Identifying sudden increases in events like failed logins, large data transfers, or outbound traffic that may indicate a brute force attempt or data exfiltration.
Examples:
- Hundreds of failed login attempts within 2 minutes.
- Sudden outbound traffic spike to a foreign country at midnight.
- Large-scale file downloads from a sensitive HR folder.
- Unusual increase in email sending volume from a single account.
Beaconing Detection
Uncovering patterns where a compromised system “calls home” to a command-and-control server at regular intervals. This subtle but dangerous activity often indicates malware infection.
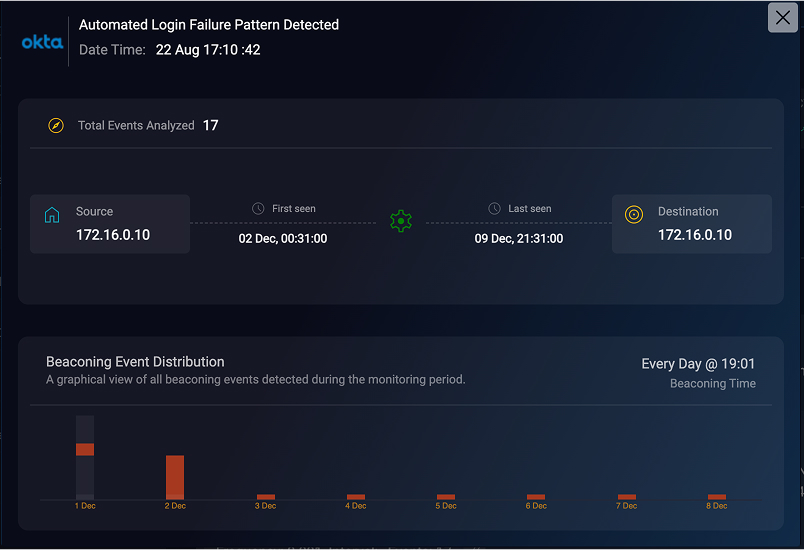
Examples:
- A workstation sending small data packets to the same suspicious IP every hour.
- IoT devices regularly “pinging” an unknown server outside the corporate network.
- A user’s laptop communicating to a domain registered only a week ago.
- Malware-infected hosts generating traffic at the exact same interval.
Impossible Travel
Detecting when a user appears to log in from two distant locations within an impossible timeframe — a strong sign of credential theft.
Examples:
- Login from India at 9:00 AM, followed by a login from the US at 9:10 AM.
- A single account logging in from VPN in Singapore and then directly from Germany in minutes.
- Privileged admin account accessed from two different continents within an hour.
- Cloud service login from London while the same user is active locally in the office.
Making Security Insights Accessible
Unlike many tools that overwhelm customers with raw logs, BinaryFlux simplifies cybersecurity. Events are displayed in clean dashboards, timelines, and charts, so security teams can quickly understand and respond without drowning in data.
By combining automation, intelligence, and clarity, BinaryFlux ensures that even complex attacks become easy to detect and mitigate.
The Future of Cyber Defense
As threats continue to evolve, BinaryFlux remains ahead of the curve, empowering organizations to defend against attacks with smarter insights and faster responses.
With innovations like behavior-based detection and automated anomaly tracking, BinaryFlux is not just a cybersecurity tool — it’s a trusted partner in safeguarding the digital future.
